- Loadbalancing multiple WAN (T1) connections
for efficient bandwidth utilization.
- High fault tolerance of enterprise/office WAN
connectivity.
- Easy setup and configuration via a web browser-based
visual console.
- Supports Frame Relay and HDLC protocols.
- Comprehensive bandwidth management on the WAN
link, using the advanced QoS module allowing incoming and outgoing
traffic to be managed.
- Eliminates the need for additional router or
gateway.
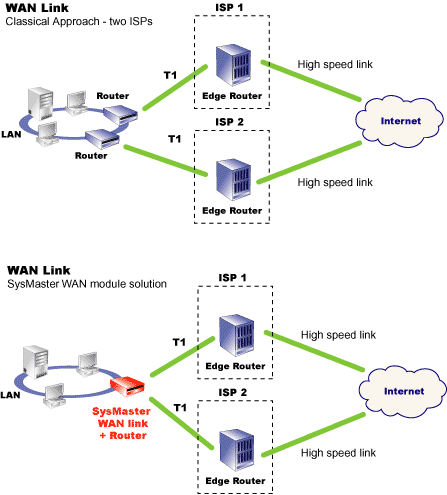
Why WAN link Loadbalancing?
Many businesses opt to lease several WAN (T1) lines
from separate ISPs, for increased availability and protection. Several
ISPs are often used to protect against total failure; if one ISP
goes down, the other ISPs can pick up the slack. However, separate
T1 connections are underutilized and improperly balanced, which
hinders speed and limits optimization.

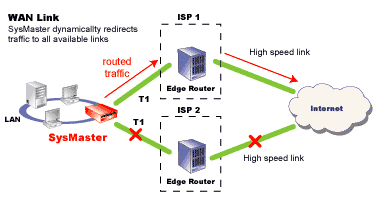
The SysMaster WAN link module integrates the multiple
T1 lines into one link and balances the traffic among the available
WAN interfaces. The loadbalancing algorithm use per connection granularity
(i.e. when a client establishes a connection with an external server,
all IP packets within this connection are exclusively forwarded
through the same T1 interface and respectively to the same ISP provider).
As a result, SysMaster provides full utilization of all available
WAN lines with improved fault tolerance.
Comprehensive WAN Connectivity Solution
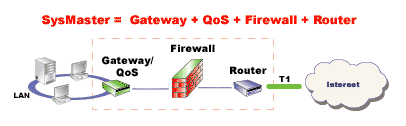
The SysMaster WAN link module provides sophisticated
WAN connectivity to offices and enterprises. It enables network
administrators to build efficient Internet connectivity solution
as a base to building efficient VPNs and extranets. A SysMaster
device WAN link module can be bundled with several independent CSU/DSU
modules for T1 connectivity. Together with the Router/Gateway, Firewall
and QoS modules, SysMaster offers the ideal solution for office/enterprise
WAN connectivity and provides robust performance coupled with high
level of efficiency, reliability and security.
Intelligent WAN Link Fault Tolerance
SysMaster is capable of filtering traffic based
on source/destination IP addresses, IP network masks, IP/TCP/UDP
ports, packet types and more. It can be configured to accept limited
traffic from specific addresses or completely prohibit all access.
In addition, specific TCP/UDP traffic, or any application based
on these protocols can be restricted. Advanced mechanism for flood
detection, such as SYN flood, PING flood and others, allows for
quick isolation of malicious attacks.
|